고정 헤더 영역
상세 컨텐츠
본문

Phase 3: Onto Meterpreter Again: Oops I did not remember that Before Pressing that final carry on you should proceed onto meterpreter and check that, for how very much time the telephone has not been used(is usually nonproductive), you can do that by typing:. idletime. BUT HERE Comes along THE Issue, THE idletime order does not function on android, so you cant tell if the consumer is making use of the telephone currently or not.
(However there are other complicated methods. Like examining RAM étc.). But nevermind wé will continue to exploit and take the risks. Type: dumpsms to collect/dump all the communications to root folder. (You can furthermore style: dumpcontacts for more exploitation). Stage 6: Remove the Message: Nope, You cannot remove the message until the hacked mobile phone is rooted. If rooted type: delete information/data/com.android.providers.telephone/databases/mmssms.db Caution!
Hack Fb Lewat Inspect Elemen
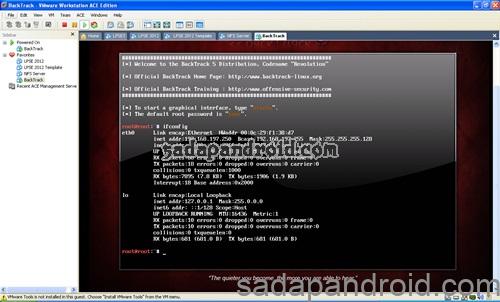
Aplikasi Hack Facebook Untuk Pc
If you wear't remove the information the Consumer will obtain dubious and will obtain to know something'h incorrect. (Beware of the Cyber Law enforcement) The Finish, Now that you have hacked google accounts, you can háck facebook for sure or any various other account. You can also spoof messengers Iike FBmessenger or WhátsApp etc.(don't type anything or the consumer will get suspicious) Thank You, N.E.A new.L. Buckeroo, You can also allow default administrator by opening cmd with ádmin privilages by writing:. online user owner /energetic:yes (just for screening).
After that record into the (default) supervisor account. Goto M: Home windows System32. Rename sethc to 123.
Cara Hack Fb Lewat Android
Create a copy of cmd found there, rename this copy as sethc. Goto the logging screen, press change 5 instances(or more). And Growth! Cmd pops-up with program(highest) priviliges. EDlT: You can confirm by typing explorer.exe, push enter. EDIT: After its comprehensive goto start and observe the title of the accounts.
Use this method as a check, until then I'll research for some various other instructions that enables boot display on your HP.




